Ring Topology: Understanding the Circular Network Configuration
When it comes to computer networking, the topology of a network plays a vital role in determining its overall structure and organization. In this regard, the ring topology is a popular network topology that is characterized by a circular arrangement where each device is connected to precisely two neighboring devices, thus forming a closed loop. This topology is widely used in modern networking landscapes due to its various advantages, such as ease of installation, fault tolerance, and efficient data transmission. However, it also has some drawbacks, including limited scalability and potential performance degradation in large networks. This article provides an in-depth look at the ring topology, covering its definition, components, protocols, advantages, disadvantages, and applications in different networking scenarios.
Understanding Ring Topology
Definition of Ring Topology
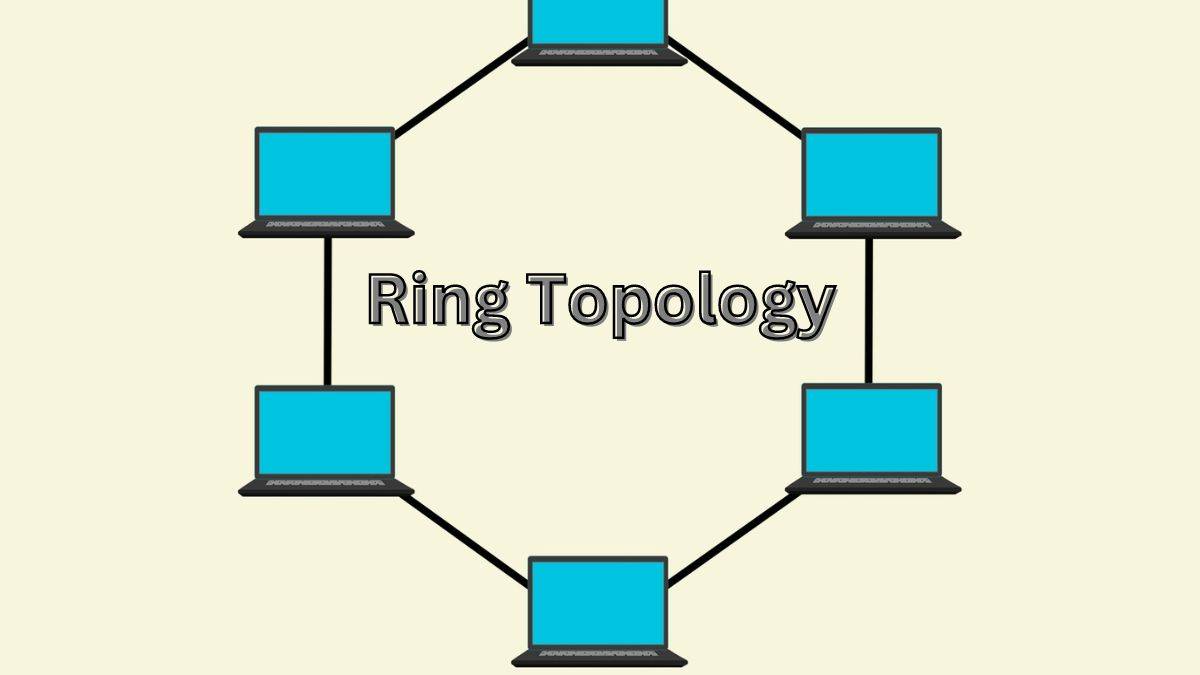
A ring topology is a type of network configuration where all the devices are connected in a circular arrangement, forming a closed loop. Each node in the ring is connected to precisely two neighboring devices, creating a unidirectional flow of data that travels along the ring, passing through each node until it reaches its destination. The circular nature of this topology ensures that there is no clear beginning or end, with data circulating continuously within the loop. This setup is often used in local area networks (LANs) where a small number of devices need to communicate with each other reliably and efficiently.
Components of Ring Topology
A ring topology is a type of computer network topology where all nodes are connected in a circular configuration. The key components of a ring topology are nodes, media, and interface cards. Nodes refer to the devices that are connected within the network, such as computers, servers, or network switches. The transmission media, such as Ethernet cables or fiber optics, link these nodes together, forming the physical ring structure. Each node is equipped with an interface card, which enables the device to connect to the transmission media and facilitates the transmission and reception of data packets within the network.
Advantages of Ring Topology
Simple Design and Implementation
Ring topology is a network configuration characterized by a circular arrangement of nodes, where each node is connected to exactly two other nodes, forming a continuous loop. One of the main benefits of this topology is its simplicity of design and implementation. Due to its straightforward layout and minimal hardware requirements, setting up a ring network is relatively easy and cost-effective, especially for small to medium-sized networks. This topology also simplifies the wiring process, as the circular arrangement of nodes eliminates the need for complex cabling schemes.
Efficient Data Transmission
In a ring topology, devices are interconnected circularly, forming a loop. Data transmission in this topology occurs sequentially, with each node receiving data packets and forwarding them to the next node until they reach their destination. This unidirectional flow of data ensures efficient transmission, as there are no collisions or contention for network bandwidth. Each device acts as a repeater, regenerating the signal and forwarding it to the next device in the ring. This ensures that the signal maintains its strength and quality as it travels around the loop. Additionally, all nodes in the ring have equal access to network resources, resulting in balanced data traffic across the network. This topology is widely used in local area networks (LANs) and is suitable for relatively small networks with low to moderate traffic.
Disadvantages of Ring Topology
Single Point of Failure
Ring topology is a highly efficient network configuration that is commonly used in computer networks. However, it has a major drawback – it is prone to a single point of failure. This means that if any node or connection within the ring fails, it can have a catastrophic impact on the entire network, causing data transmission to come to a complete stop. Unlike other topologies where multiple paths exist for data to travel, the closed-loop structure of a ring topology leaves little room for redundancy, making it highly vulnerable to disruptions. Therefore, it is necessary to carefully consider the risks associated with ring topology before implementing it in any network.
Limited Scalability
Ring topology is a popular network configuration that connects multiple devices in a circular pattern. However, it has a few limitations that need to be considered. One such drawback is its limited scalability. Although adding new nodes to the network is relatively straightforward, expanding the ring beyond a certain size can pose significant challenges. As the number of nodes increases, the latency and overhead associated with data transmission may also rise, which can lead to performance degradation. Moreover, reconfiguring the network or adding new connections to accommodate growth can be complex and time-consuming. Therefore, it’s essential to weigh the pros and cons of a ring topology carefully before implementing it in your network infrastructure.
Ring Topology Protocol
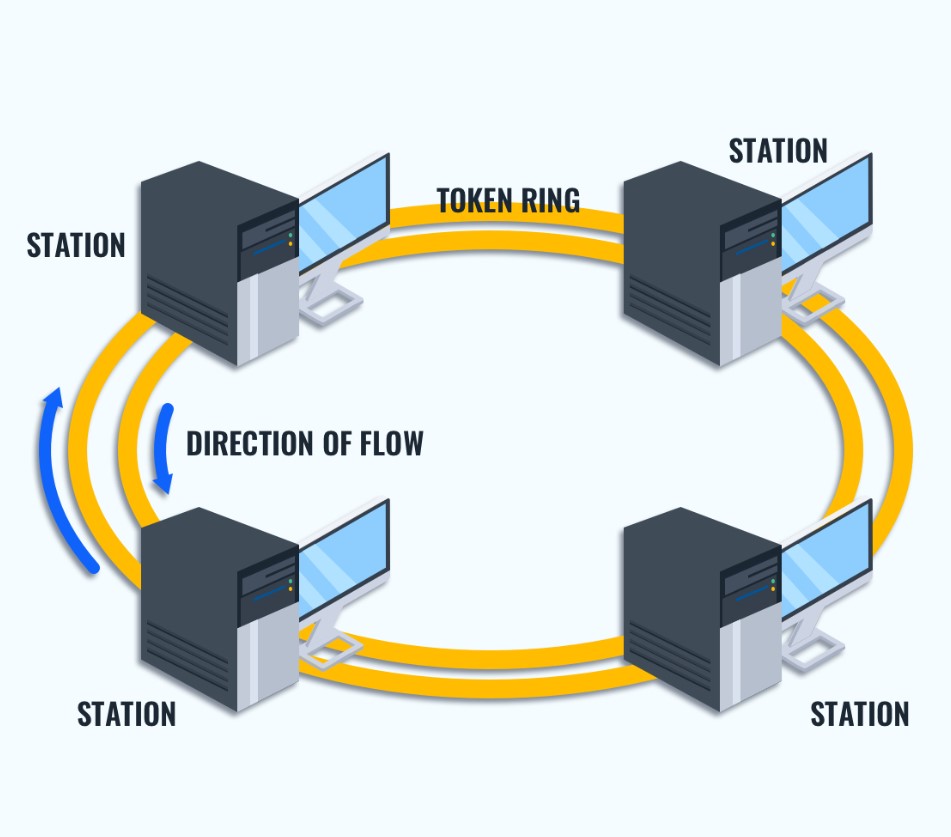
Token Passing Protocol
In a ring topology, which is a network configuration where nodes are connected in a circular pattern, data transmission is regulated by a communication protocol called token passing. This protocol involves the circulation of a special token, which serves as a permit for nodes to transmit data on the network. Only the node that currently possesses the token is permitted to transmit data, ensuring that communication is orderly and controlled within the ring. Once a node has completed transmitting its data, it passes the token to the next node in the ring, allowing it to send its data packets. This method of data transmission is highly effective in ensuring that only one node transmits data at a time and that each node has an equal opportunity to transmit data in a fair and organized manner.
Data Transmission Process
The process of data transmission in a ring topology follows a predefined sequence, dictated by the token passing protocol. When a node wishes to transmit data, it waits for the token to arrive at its location. Upon receiving the token, the node attaches its data packet to the token and forwards it to the next node in the ring. Each node examines the data packet as it passes through, extracting any relevant information or forwarding it to the next node until it reaches its destination. This sequential transmission ensures that data flows continuously around the ring without interruption.
Examples of Ring Topology
Token Ring Network
Ring topology is a network architecture where each node is connected to its neighboring nodes in a logical ring formation, with data transmission regulated by token passing. One of the most well-known examples of this topology is the Token Ring network, developed by IBM in the 1980s and adhering to the IEEE 802.5 standard. In a Token Ring network, data circulates in a unidirectional manner, resulting in a deterministic and reliable behavior that made this topology widely used in enterprise environments.
Fiber Distributed Data Interface (FDDI)
Fiber Distributed Data Interface (FDDI) is a type of ring topology that is specifically designed to provide high-speed connectivity and fault tolerance in large-scale networks. FDDI networks make use of fiber optic cables to create a high-speed ring backbone, which is capable of supporting data rates of up to 100 Mbps. This topology makes use of dual counter-rotating rings, which ensure redundancy and fault tolerance in case of cable breaks or node failures. Due to its high reliability and uptime, FDDI was extensively used in mission-critical applications.
Comparison with Other Topologies
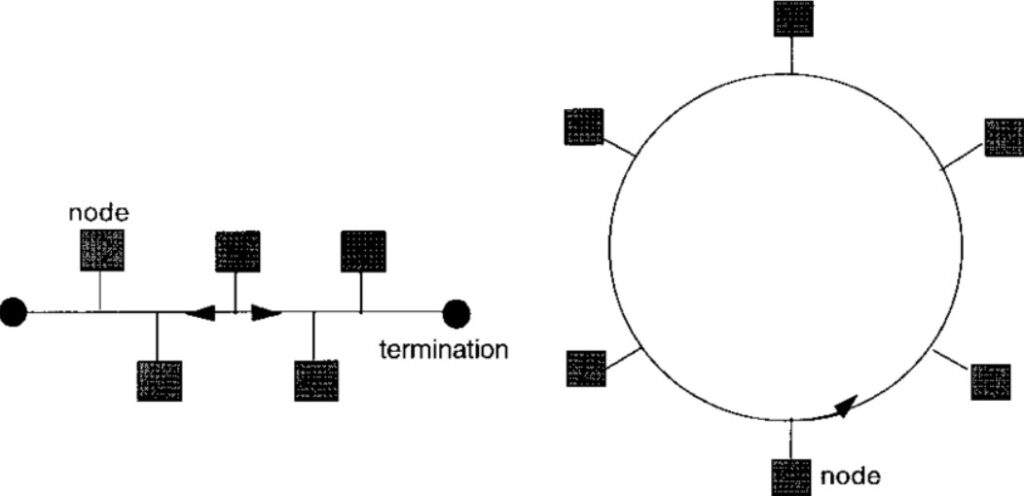
Ring vs. Bus Topology
When it comes to different types of network topologies, some key differences set them apart. One such example is the comparison between ring topology and bus topology. In a bus topology, all the nodes are connected to a single communication line, with data transmitted to all nodes at the same time. This often leads to data collisions and contention for network bandwidth, especially in larger networks. On the other hand, in a ring topology, data is transmitted sequentially along the ring, which eliminates the risk of collisions and provides better control over data transmission. Ring topology also allows for network segmentation, which makes it possible to create smaller independent rings within a larger network.
Bus Topology: Exploring the Backbone of Network Connectivity
Ring vs. Star Topology
There are a variety of network topologies used to connect multiple devices, each with its advantages and disadvantages. One popular topology is the star topology, in which each node is linked to a central hub or switch. This design makes it easy to add new nodes to the network without disrupting existing connections, providing excellent scalability and flexibility. However, one major drawback of the star topology is its reliance on the central hub, which can cause the entire network to fail if the hub malfunctions.
In contrast, the ring topology is designed to distribute the responsibility for data transmission across all nodes in the network. This approach minimizes the impact of node failures, making the network more resilient overall. Ring topology also offers efficient data transmission without the need for a central coordinating device, which can be beneficial in certain scenarios. Ultimately, the choice of network topology will depend on the specific needs of the network and its users.
Star Topology: Illuminating Network Connectivity
Implementing Ring Topology
Physical Layout Considerations
When setting up a ring topology, it is important to consider various physical layout factors. Proper cable routing and installation are essential for ensuring optimal performance and reliability of the network. A well-planned configuration must be implemented to avoid any breaks or interruptions in the transmission media. Additionally, the placement and connectivity of nodes are crucial as they can impact the strength of the signal and the speed of data transmission. Careful attention to these factors can help to ensure that your ring topology network operates efficiently and effectively.
Network Configuration and Setup
When setting up a network, the first step is to establish the physical layout. Once this is done, the network configuration and setup process can begin. This involves using various configuration tools and software to define network parameters such as node addresses, routing tables, and access control policies. To ensure that the network is functioning correctly, testing and troubleshooting procedures are employed. This may include conducting connectivity tests, monitoring network traffic, and analyzing performance metrics for optimal operation. By following these procedures, potential issues or bottlenecks can be identified and addressed, ensuring a smooth and reliable network performance.
Maintenance and Troubleshooting
Routine Maintenance Tasks
To ensure a ring topology network continues to operate at optimal levels of performance and reliability, routine maintenance is crucial. Among the key tasks that need to be carried out are cable inspection and replacement, as damaged or degraded cables can result in signal loss or data corruption. In addition, it is important to monitor the nodes and diagnose any issues with individual connections. Regular maintenance helps prevent downtime and ensures that the network remains operational at all times.
Common Issues and Solutions
Ring topology networks are known for their efficiency, however, they are not completely immune to problems. In case of any node failure or ring breakage, there can be a disruption in data transmission leading to downtime. Additionally, cable damage or interference can cause signal degradation and data loss. It is important to take prompt action in such cases to diagnose and resolve the issue. This may involve identifying the faulty node or segment of the ring, repairing or replacing damaged cables, and reconfiguring the network to restore connectivity.
Future Trends and Innovations
Evolution of Ring Topology
As technology advances, the ring topology is expected to evolve and adapt to meet the changing demands of modern networking environments. With integration with modern technologies such as wireless networking, IoT devices, and edge computing, the future of ring topology is likely to be shaped. Moreover, advancements in network protocols and communication standards will continue to enhance the efficiency and reliability of ring topology networks, making them suitable for a wide range of applications. Ring topology is an evolving technology that promises to deliver significant benefits to the networking industry in the future.
Emerging Alternatives and Hybrid Solutions
The networking industry is witnessing the emergence of alternative and hybrid solutions, in addition to the traditional ring topology networks. One such solution is mesh topology integration which combines elements of ring, star, and mesh topologies. It offers increased flexibility and fault tolerance, making it an attractive option for organizations. Another innovation in the networking industry is software-defined networking (SDN) integration which enables centralized management and control of network resources, enhancing scalability and agility. These advancements are reshaping the networking landscape, providing new opportunities for organizations to build robust and resilient networks.
Conclusion
In the field of networking, ring topology is a crucial concept that plays a significant role in facilitating data transmission between various connected devices. Although it has certain limitations, this type of topology offers several benefits, including high reliability, improved efficiency, and fault tolerance. By gaining a thorough understanding of the key characteristics, advantages, and challenges of ring topology, organizations can make informed decisions about network design and implementation, thus ensuring the smooth operation of their digital infrastructure.